Compliance as a Service

Solutions for Every Journey
We understand that every organization is different and has unique compliance needs. That’s why we offer a variety of solutions to meet you where you are in your journey — no matter the framework.
Many independent software vendors (ISVs) need help building a business case and may not fully understand the rigor of authorization. Project Hosts can help you get started affordably, move at your own pace and easily transition into full authorization when you’re ready.
Programs like Early Start are a great way to gain momentum and lay the foundation for later success.For ISVs with executive sponsorship and a plan to manage the process, Project Hosts’ full authorization programs can help you cross the finish line.
With our connections and expertise, you can secure a sponsor, implement security controls, complete the audit and achieve authorization in 8 months or less.
Our Approach
We take a personalized approach to compliance, working closely with you to understand your specific needs and goals. Our team of experts will guide you through the entire process, from initial assessment, thru authorization onto continuous monitoring.
Gathering Interest
No pipeline? No problem.
Many independent software vendors (ISVs) need help building a business case and may not fully understand the rigor of authorization. Project Hosts can help you get started affordably, move at your own pace and easily transition into full authorization when you’re ready. Programs like Early Start are a great way to gain momentum and lay the foundation for later success.
Starting Your Initiative
Solidifying your business case?
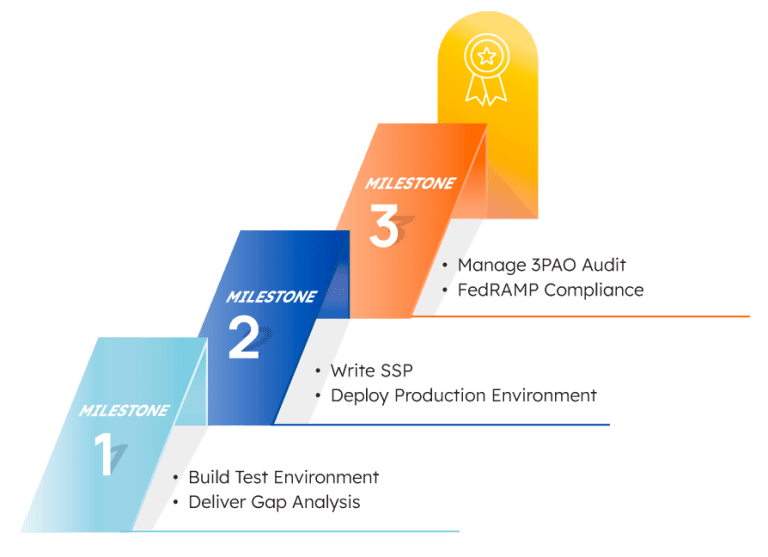
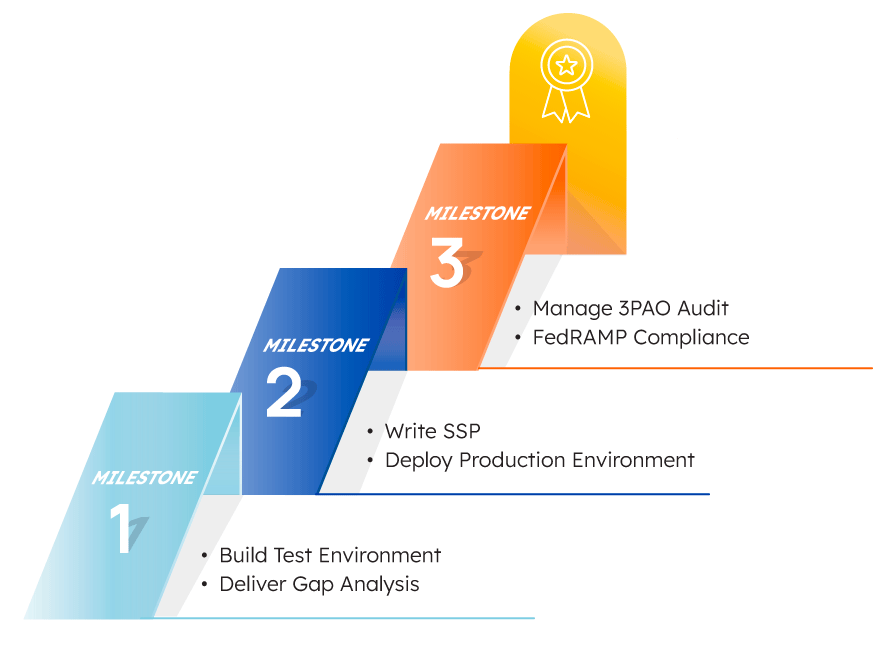
Solutions like Project Hosts’ Milestone and Compliance Readiness programs can help you take the next step. These programs don’t require an agency sponsor and can help you shorten the timeline toward full authorization for maximum cost-efficiency. They can also help improve your chances of securing a sponsor in the future — one of the biggest roadblocks in the journey.
Charging Ahead
Ready to get started?
For ISVs with executive sponsorship and a plan to manage the process, Project Hosts’ full authorization programs can help you cross the finish line. With our connections and expertise, you can secure a sponsor, implement security controls, complete the audit and achieve authorization in 8 months or less.
